Process
Our cyber hedgehog platform includes the process of data collection from a wide range of sensors by our EdgeCOM. This processes and forwards the information to the server in a data protection-compliant, secure and environmentally friendly manner. The data is stored on the server and can be visualized on our portal.
Edge Computing
Local data processing is the future!
With edge computing, a computer collects and processes environmental, traffic and lighting data locally in the network, for example at luminaires. Local processing enables real-time applications to be implemented and only small amounts of data to be forwarded, taking data protection into account.
efficient
energy saving
low data volumes
Highest security for your protection
Our Cyber Hedgehog platform is designed to provide maximum security. With a wide range of security features, we set the standard for protecting your sensitive data:
- an extra secured area (Trustzone) directly on the EdgeCOM protects sensitive data from unauthorized access,
- encryption/decryption prevents software and data from being tapped or manipulated,
- only authorized and signed software will run on your EdgeCOM,
- Secure Boot: each time the device is restarted, the device is checked for compromised software and only unmodified software is started and
- a permanently integrated memory (eMMC memory) prevents easy removal and thus theft or replacement of the operating software.
One gateway for everything
The EdgeCOM is characterized by its multiple connection options, which allow a wide range of sensors and applications to be combined. These include:
- PoE
- RS485
- USB
- Ethernet
- LTE/5G, Wifi und Bluetooth
- GPS
With this series of connections we offer you the flexibilityto seamlessly integrate a wide variety of devices and technologies. Due to the variety of connections, multiple sensors can be connected to one EdgeCOM. It thus combines many conventional gateways into one and contributes to sustainability .

Maximum Performance
The EdgeCOM enables data to be processed locally and results to be transmitted in a resource-efficient manner. It also enables prioritization of real-time applications and machine learning. With our platform, powerful capabilities are available to take your applications to the next level.
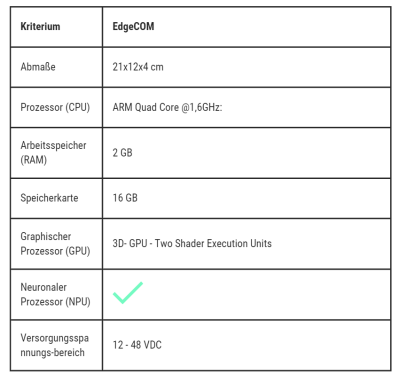

The next generation of gateways
Compared to conventional gateways, the EdgeCOM offers a number of key advantages that take our applications to a new level. With our advanced features, we set the standard for industry-standard performance, security and quality.
- Higher Cyber Security
- Greater capacity to act
- Higher quality in industry standard
- Fewer hardware components (gateways) required
With our EdgeCOM, you benefit from more cost-effective, resource-efficient, lower-maintenance and more stable solutions compared to conventional gateways. Our platform provides you with the necessary features to run your applications efficiently and securely.
Feel free to contact us to learn more!
Server-Architecture
Data transfer securely from A to B
For the reliable transmission of data from the EdgeCOM to a defined server, we use M2M SIM cards in combination with an access-restricted SSH procedure (secure shell). SSH provides an encrypted connection between the EdgeCOM and the server, protecting your data from unauthorized access and ensuring the security of the transmitted information. In addition, SCF ensures the following general conditions as part of the cyber security concept:
- firmly defined point-to-point communication
- Up-to-date authentication & encryption method with one random & automatic key exchange per connection between device and server and between devices
Flexible server-architecture for any application
To ensure a high level of security for the stored data, SCF's cyber hedgehog concept prevents devices from accessing the database directly. Containers are interposed in each case to create another "security wall" and make access more difficult.
The state-of-the-art, maintained container architecture makes it possible to react flexibly to the needs of the project and to plan various ON-premises as well as full-services implementations. The architecture takes into account a variety of protection mechanisms against a wide range of attack vectors, such as the man-in-the-middle attack. The entire solution is GDPR compliant and meets current industry cybersecurity requirements.


